Public Key Encryption and Public Key Infrastructure - Explained
What is this Public Key Encryption and Public Key Infrastructure? It is simply the single most effective method for securing a public communications networks, and is used throughout the world for the transmission of sensitive data. The Army, Navy, and Airforce use PKI. Government agencies use PKI. Financial and medical institutions use PKI. And now you can too. That's because Safe-mail incorporates PKI at every possible point in its infrastructure.
Safe-mail is a secure communication environment. Everything you are doing inside Safe-mail is secure. Safe-mail is a web-based communication system that is accessible at any time from any location using almost any type of communication device. Safe-mail has the highest security without sacrifice to ease of use and mobility. There is no need for downloads, installations, setup or even cookies to use Safe-mail.
The most common way to use Safe-mail is via a browser such as Explorer or Netscape. However, Safe-mail's e-mail functions can also be accessed by e-mail clients such as Outlook etc. We support email clients via POP and IMAP. We recommend IMAP because of greater security and because of improved environment. We recommend POP is used only to check if there are any new messages. The disadvantage of e-mail clients besides being able to access only the e-mail functions of Safe-mail, is that they need some setup and therefore are less mobile.
Safe-mail is seamlessly compatible with many communication standards including POP, IMAP, SMTP and MIME and their secure variations. S/MIME, which is the PKI implementation for e-mail, requires the Private Key and Digital Certificate of the sender plus the Digital Certificates of all the recipients to be available at all times. Safe-mail's Certificate Servers automatically record all incoming certificates of non-Safe-mail users and make them available to all of Safe-mail's users. With the Safe-mail system, Safe-mail's Certificate Server manages and utilises everyone's Digital Certificates. Because this administration is managed automatically in the background, the user is completely unaware and shielded from what's happening.
Safe-mail is a unique implementation of PKI from two major viewpoints:
Web-based
Safe-mail is implemented on a server accessible via the Internet. Every user that opens an account at Safe-mail is assigned his/her own space. We call that space the Virtual Secure User Space (VSUS). Each VSUS is accessible only to its owner. The Private Key and the Digital Certificate of the user are installed in the user's VSUS and the Private Key is protected by the user's password. A copy of the user's certificate is also kept in Safe-mail's Certificate Server.
This design ensures that the user cannot loose his Private Key due to the usual causes of loosing digital data, i.e. disk crash, careless installation of a new OS version, theft etc. Equally, this design ensures true mobility since the private key is not installed on the local PC.
Completely automated and seamless operation
A common mistake made by many is to say that PKI is automated. Real life experience proves one thing to anyone who ever tried to use PKI: PKI is a huge pain to all parties involved. Certificate Authorities, senders and recipients all have a burden that is so intense that there is virtually no PKI implementation for regular e-mailing.
With Safe-mail, PKI becomes absolutely invisible to all parties involved.
For Individuals:
Individuals using Safe-mail have only one thing to do to be PKI compliant:
use this form to apply for a Digital Certificate.
For Organizations:
Organizations simply have to use the Digital Certificates of their clients
to communicate securely using PKI. There is no need to issue, renew or
otherwise managed Digital Certificates.
Certificate
Authority:
Safe-mail is acting as Certificate Authority and performs all the
centralized functions of the PKI system: issuing, renewing and revoking.
It is easy to be confused by some of the descriptions of PKE and PKI. We know, because we've had our own head-scratching moments too. But, take a few moments to describe the underlying concepts before getting too technical.
First of all, remember that Public Key Encryption is based on some VERY advanced mathematical breakthroughs. To understand the math... let's just say that you'll need a couple advanced degrees to get the details straight. (And, we never ask explanations from mathematicians. It's a good way to get confused.)
However, as long as you stay away from the mathematics, PKE is pretty easy to understand. Anyone who has ever left their keys in their hotel room has come face-to-face with a part of the PKE idea.
The central point behind PKE is this:
The way that you lock doesn't need to be the way that you unlock.
For instance it is possible to buy a safe that requires one key to lock the safe door, and another key to unlock it.
That is PKE.
Let's try out a few examples, and see if they help our understanding.
Billy Bobb's Diner
Billy Bobb, the owner of Billy Bobb's Diner has a problem. He has been asking family and friends to create new recipes for his diner. He's been doing this for years, and the result is that he has the best diner in town. His problem is the competition, which has been stealing the recipes that are being sent to him. He doesn't know how they are doing it, and he's puzzled over the problem for months. But, after reading about PKE and PKI, Billy Bobb had found a solution.
He created a new kind of package for his recipe-creators to use. The new package contains two locks, one lock for closing the package, another lock for opening it. The first lock, he called the "public" lock, and the other lock he called the "private" lock.
He then created two different keys. The first was a public key that he would hand out to everyone, and he made lots of them. In fact, everyone who entered his diner was given one - along with a box. Whenever someone wanted to send him a recipe, they put it in the box and locked it with the "public" key. After the package was locked, no one could open it except Billy Bobb - using his own "private" key.
When Billy got the package, he took out his private key, inserted it into the "private" lock on the right, and opened the box to get the recipes.
His competition could no longer steal his recipes.
That's PKE

Phil's Baggage Claim
Phil runs the long term baggage storage area at the Benjamin Harrison Memorial Airport in Wisconsin. He's been trying to find a way for customers to store their own bags, while making sure that they pay when they pick them up. Phil was reading about PKE, and realized that he had the solution to the problem. Phil installed two locks in every storage locker. One of the locks was for the public key. The other was for the private key that only Phil had. When travelers put their luggage in one of the lockers, they closed the locker with the public key. When it came time to pick up their luggage, travelers would come to Phil, who would go to their locker and open the locker using the private key.
That is PKE.
back to the topPublic Key Infrastructure - PKI
Okay, you have the picture. So, what is this PKI? As we said before, PKI stands for Public Key Infrastructure, and it is the system that supports Public Key Encryption. Simply put, you need a central repository for all the Public keys that have been created. If you want to send an email to someone using PKE, you need to use the PKI. This means going to a Public Key Server that holds all the public keys.
Paul and Betty
When Paul wants to send an email to Betty, he goes to the closest Public Key Server, and looks up Betty's public key. He encrypts the message and sends it on to Betty. Once Betty receives the message, she decrypts the message using her private key.
Why PKI?
To think of it another way, the public key is an encryption-only key that everyone can use to make any message secret - but can never be used to reveal the contents of a message. While the private key is a decryption-only key that only one person is able to use, because only he/she owns that key. It is the perfect solution.
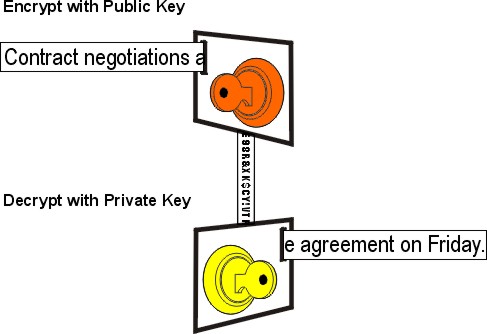
This is how PKI is normally implemented today:
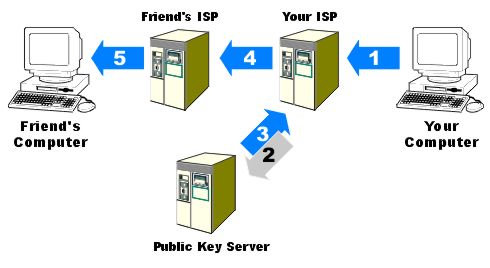
Your computer makes a secure connection with your Internet Service Provider (ISP) via SSL. Your computer passes on the message that has been prepared.
The ISP looks at the address that it needs to send the message to. Because the ISP knows that it needs to use Private Key Encryption (PKE) it goes to the Public Key Server and asks for the Public Key for the intended recipient.
The Public Key Server hands the public key over to your ISP.
Your ISP takes your friend's public key and encrypts your email message and then sends it to your friend's ISP.
Your friend's ISP takes out the recipient's private key and decrypts the message and sends it on to your friend.
Public Key Encryption (PKE) was the brainchild of two Stanford mathematicians, Whitfield Diffie and Martin Hellman, who published their discovery in 1976. Until Diffie and Hellman came along, all methods of encryption were symmetric—the key for encrypting a message was identical to the key for decrypting it. This meant that you needed to have a different key for each person that you wanted to communicate with. The bigger the list, the more that you needed to manage. At one time, loading cipher books onto a ship of the US Navy required a forklift.
The solution was to make the encryption method asymmetric - the key for encrypting the message would be different from the key for decrypting it. Diffie and Hellman were able to demonstrate the theory.
That was the idea. That was the theory, but no one could get it to work in the real world. That is due to the fact that their theories were useless without an encryption method and an infrastructure, as in: Public Key Infrastructure (PKI). And this is where three more mathematicians stepped in to save the day.
A year later (in 1977), Ronald L. Rivest, Adi Shamir, and Leonard M. Adleman, another team of mathmeticians from MIT found a way to apply Diffie and Hellman's theories in the real world. Combining the first letters of each of their last names, the named their encryption method as RSA. The basis of RSA is the understanding that when you multiply prime numbers together, there is no easy way to reduce number back to its prime numbers - and the larger the number, the more difficult it is to reduce the number.
Using the RSA method, the user can publicly distribute one of the keys, while keeping the other key private. Anyone wanting to communicate could encrypt the message using the public key, and send the message to the owner of the key where the private key would be used to decrypt and read the message. And, a Public Key Infrastructure (PKI).
back to the top
Both PGP and S/MIME are based on asymmetric encryption which in turn is based on Private and Public keys. They are therefore similar to each other but, significantly, there are profound differences between the two. These differences are the result of the fact that while S/MIME is an accepted standard by ALL modern developers and industry, PGP which might regarded as the origin of S/MIME, these days has very little support and development because it provides no advantages.
Some main differences:
With S/MIME, the symmetric encryption libraries are always the final word and the most tried and tested libraries.
back to the top